On March 21, 2025, a severe security vulnerability (CVE-2025-9.1) was disclosed in Next.js, the popular JavaScript framework. The exploit allows attackers to bypass authentication and authorization in Next.js middleware, posing a significant risk to applications relying on middleware for security checks.
How Serious Is This Vulnerability?
If you’re running an unpatched version of Next.js with middleware—especially if hosted on Vercel or Netlify—your application could be at immediate risk. The flaw enables attackers to skip middleware checks entirely by manipulating a specific header, potentially granting unauthorized access to protected routes.
Who Is Affected?
- Next.js applications using middleware for authentication or authorization.
- Apps hosted on Vercel or Netlify (self-hosted instances may also be vulnerable).
- SaaS products that rely on middleware for paywall or access control logic.
If your app does not use Next.js middleware or is hosted outside of Vercel/Netlify, the risk is minimal.
How the Exploit Works
Middleware in web frameworks acts as an intermediary layer between requests and responses, commonly used for logging, error handling, and security checks. The Next.js vulnerability stems from a misconfigured header (middleware-subrequest) that, when manipulated, allows attackers to bypass middleware entirely.
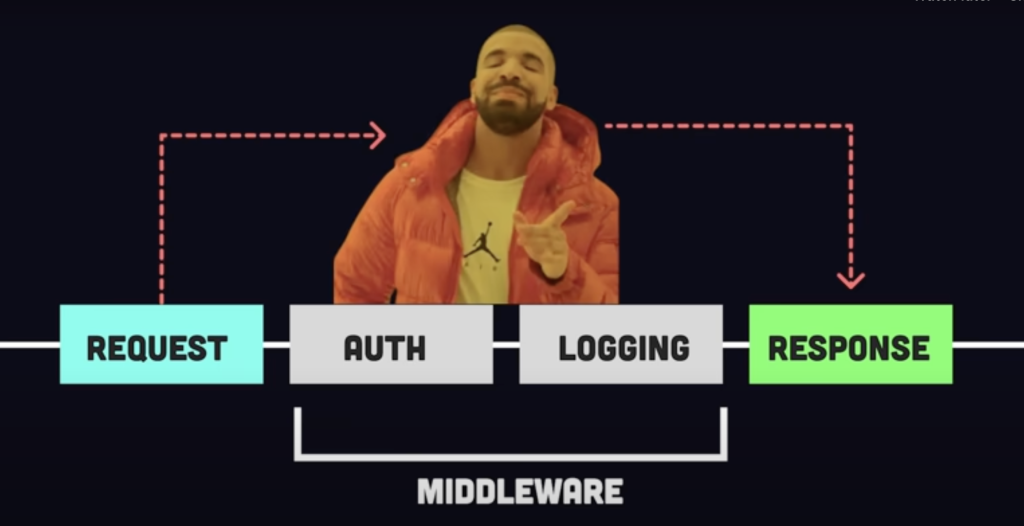
Key Details of the Exploit:
- Attackers can guess middleware names due to predictable naming conventions.
- The exploit is simple to execute, requiring only header manipulation.
- If your middleware enforces payment checks, role-based access, or authentication, attackers could bypass these protections.
Timeline of the Vulnerability
- February 27, 2025: Security researchers reported the issue to the Next.js team.
- March 18, 2025: A patch was finally released—nearly three weeks later.
The delay in fixing such a critical flaw has drawn criticism, especially since middleware is a core security feature for many applications.
Industry Fallout and “Tech Bro Drama”
The vulnerability sparked heated debates on social media, with competitors like Cloudflare capitalizing on the situation. Cloudflare’s CEO promoted migration tools to move Next.js apps from Vercel to their platform, citing better security. Vercel’s CEO fired back by referencing Cloudflare’s past security incidents (like Cloudbleed) and criticizing their DDoS protection.
While the exchange was entertaining for onlookers, the real concern remains the security of Next.js applications in production.
What Should You Do Now?
- Upgrade Immediately – Ensure you’re running the latest patched version of Next.js.
- Audit Middleware Logic – Verify that critical security checks aren’t solely dependent on middleware.
- Monitor Suspicious Activity – Look for unexpected requests with manipulated headers.
Conclusion
Security flaws are inevitable in any framework, but the severity of this vulnerability—and the delayed response—highlights the importance of proactive security measures. If you’re using Next.js middleware, take action now to prevent potential breaches.
Stay updated with official Next.js security advisories and ensure your deployments are always running the latest stable versions.